√1000以上 aws s3 access logs encryption 351628-Aws s3 access logs encryption
New Amazon S3 Encryption Security Features Aws News Blog
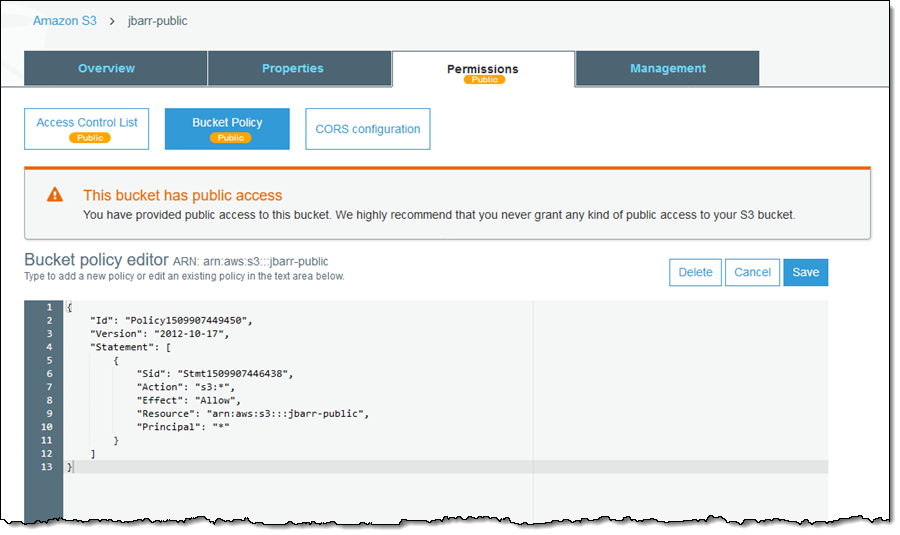
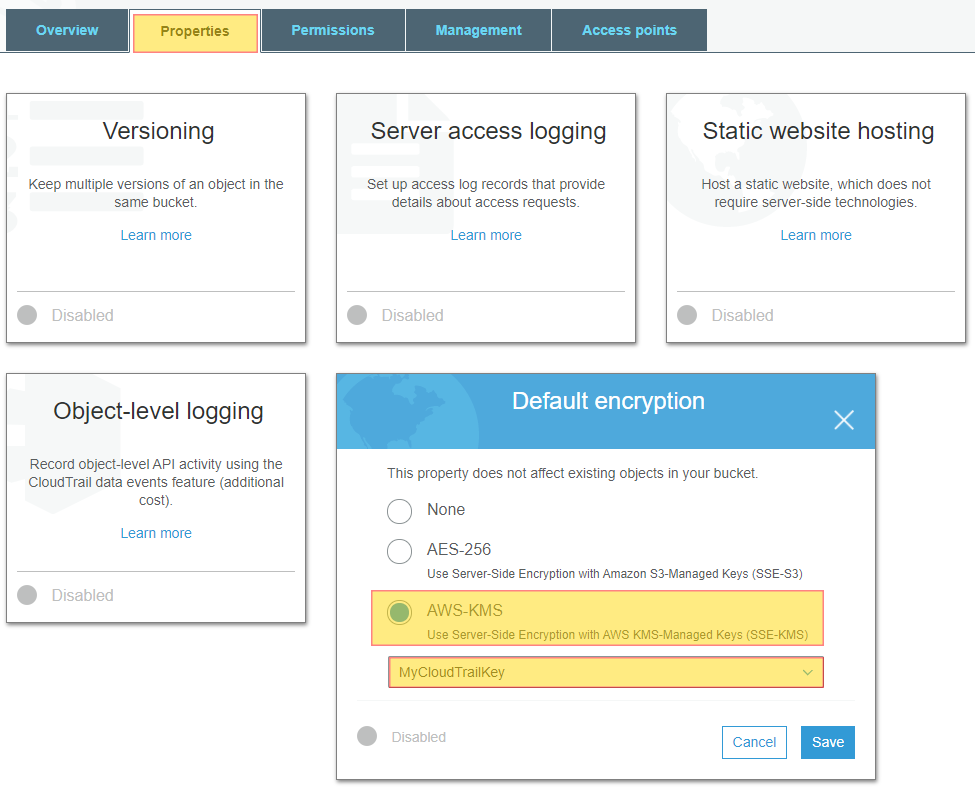
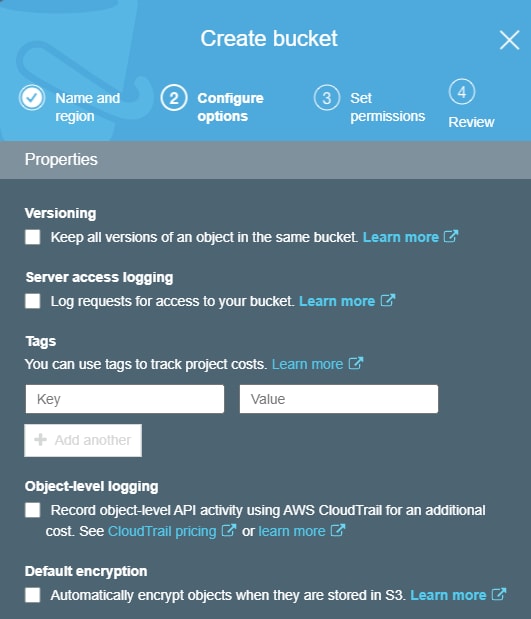
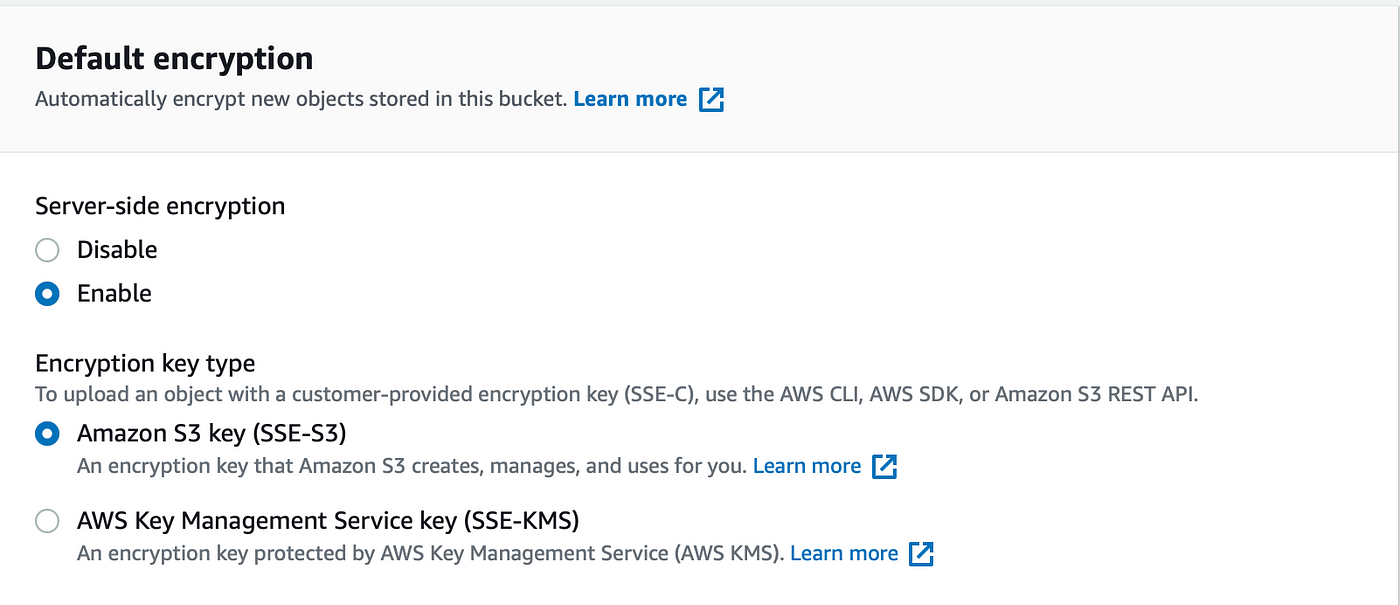
I have read/write/admin access to an S3 bucket I created I can create object in there and delete them as expected Sign up or log in to customize your list more stack exchange communities company blog amazonwebservices encryption amazons3 Share Improve this question Follow asked Sep 4 '17 at 16 nmh nmhAWS S3 security tip #5 – encrypt S3 files A very important security measure for private buckets is serverside encryption Enabling serverside encryption from S3 bucket properties The "Default encryption" will be automatically applied if an uploaded
Aws s3 access logs encryption
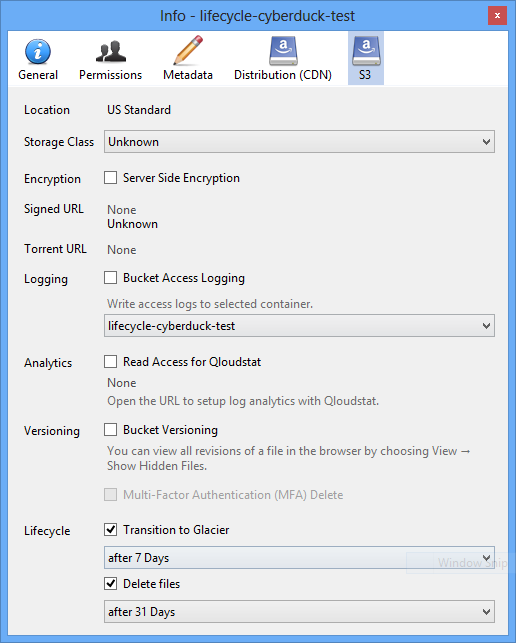
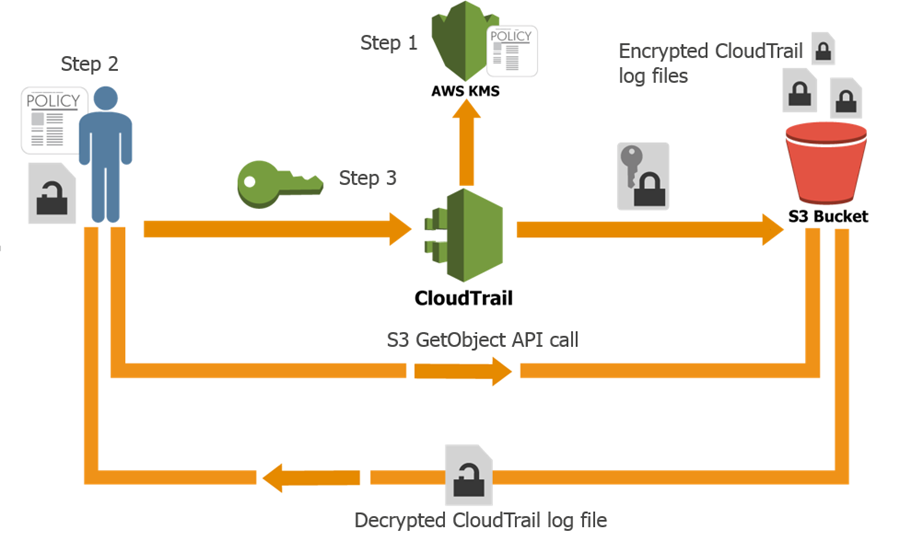
Aws s3 access logs encryption-Use the CMK to encrypt an EBS volume and attach that to a running EC2 instance for use Turn on CloudTrail for auditing purposes and deliver its logs to an encrypted S3 bucket Generate a CMK external to AWS and import it to attach and encrypt an EBS volume Disable and enable CMKs Confirm that encryption is turned on and working1 point 3 years ago I received official word from AWS today that S3 is unable to deliver logs encrypted today and they recommend you actually enable the new default encryption at the bucket level vs doing it in a policy level 2 duhaas17 1 point 3 years ago I've also confirmed this to be a decent workaround level 1

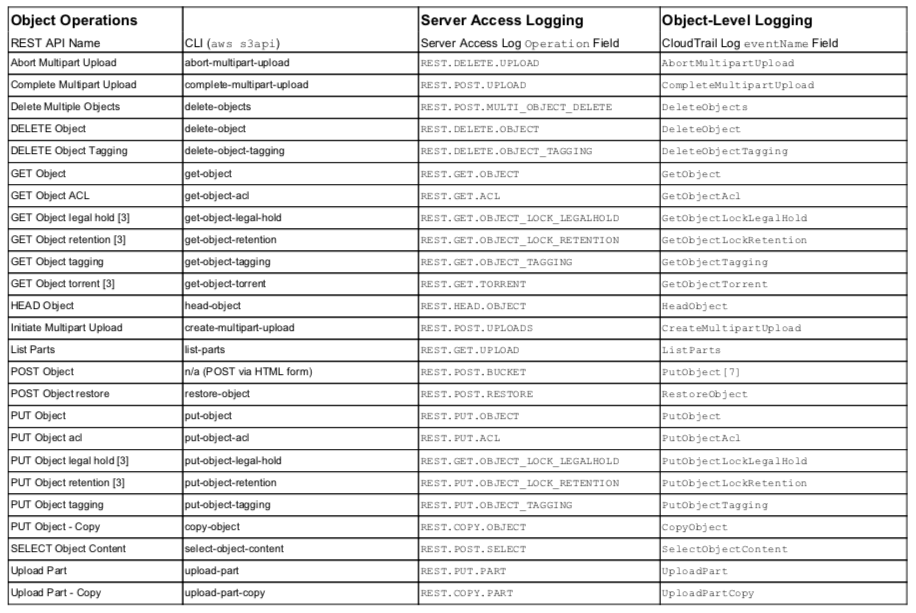
Api Aws S3 Server Access Event
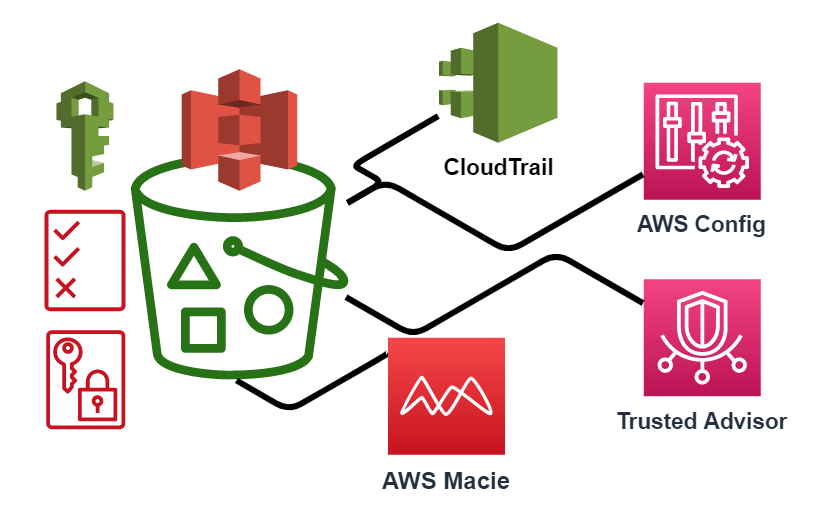
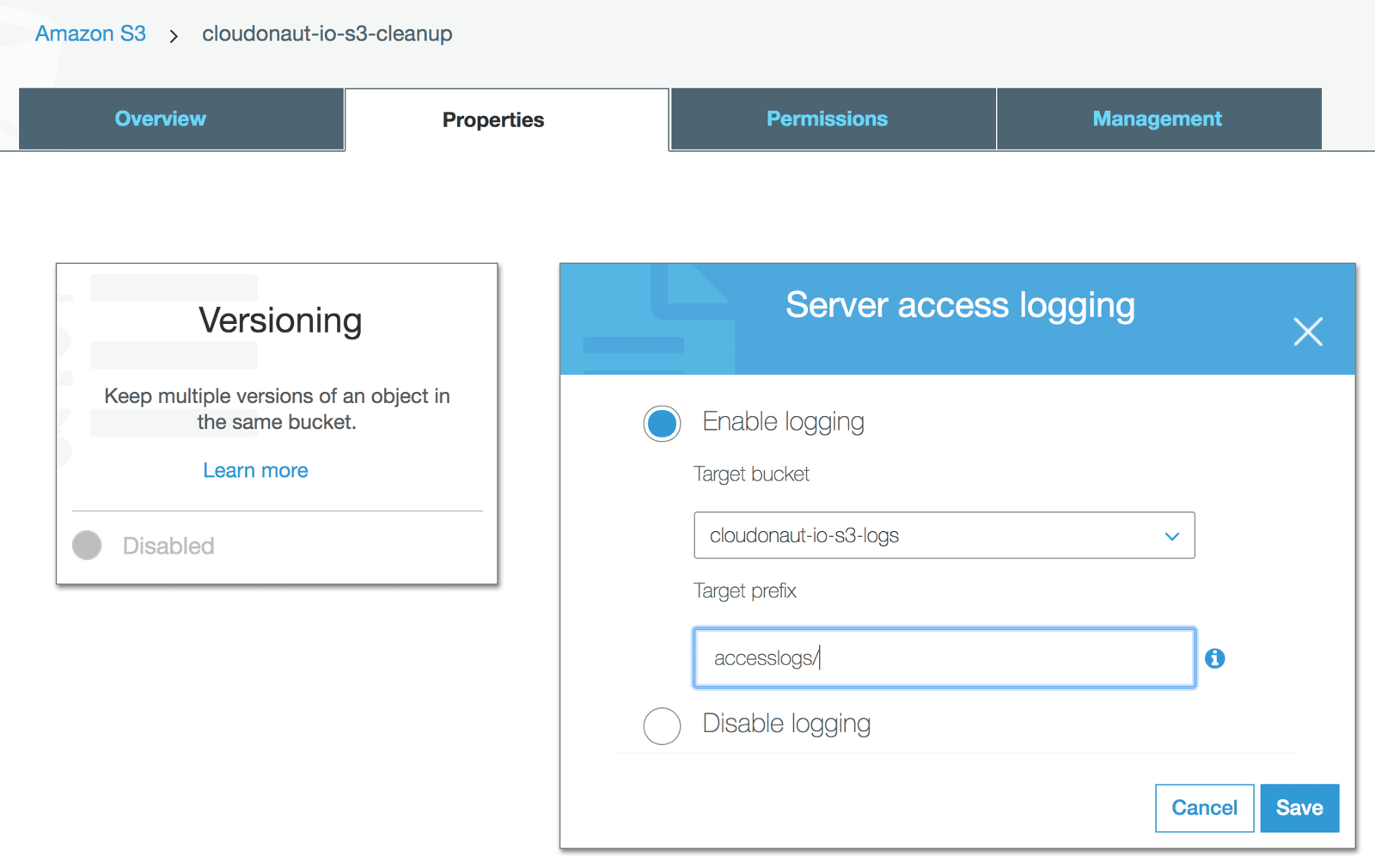
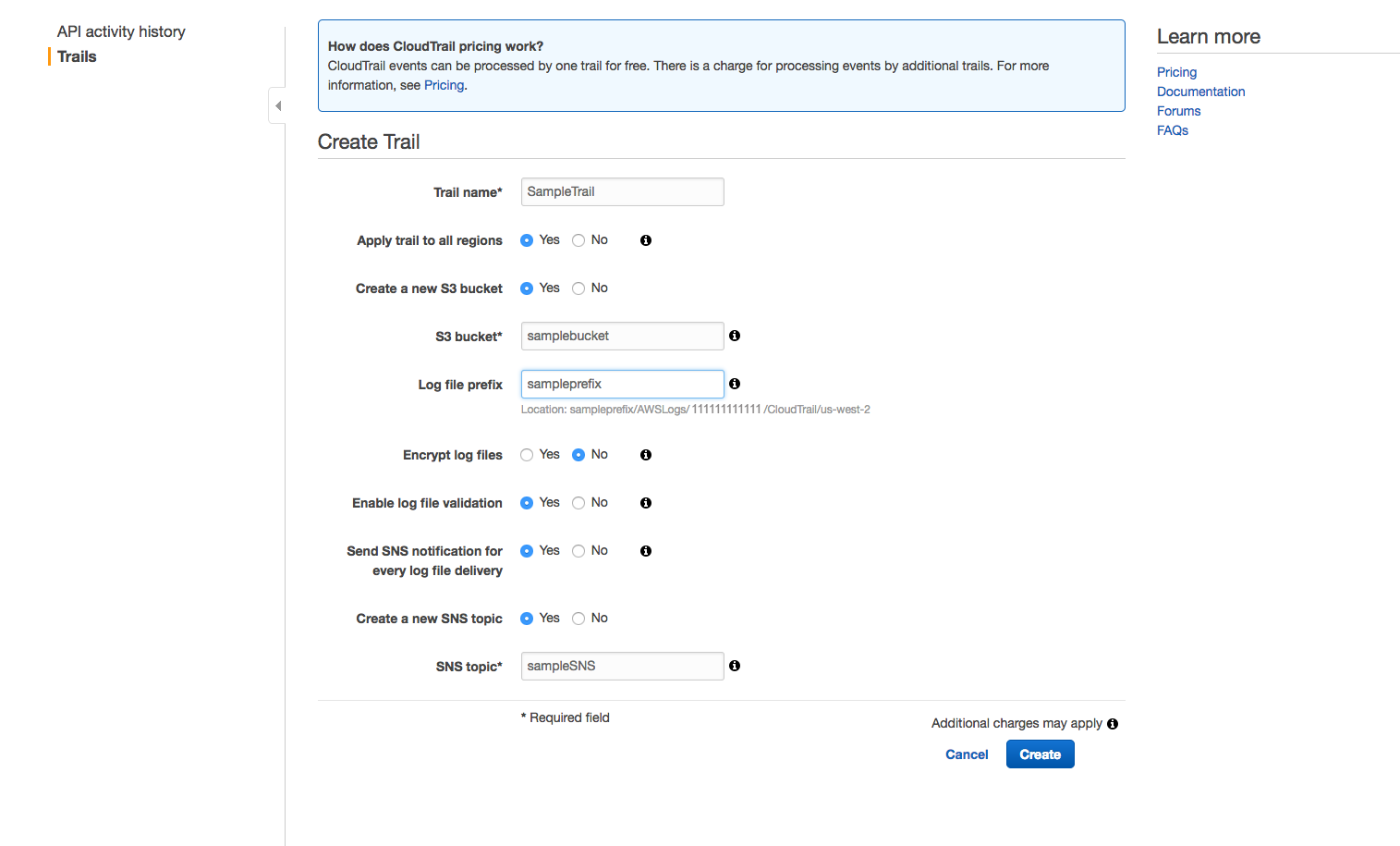
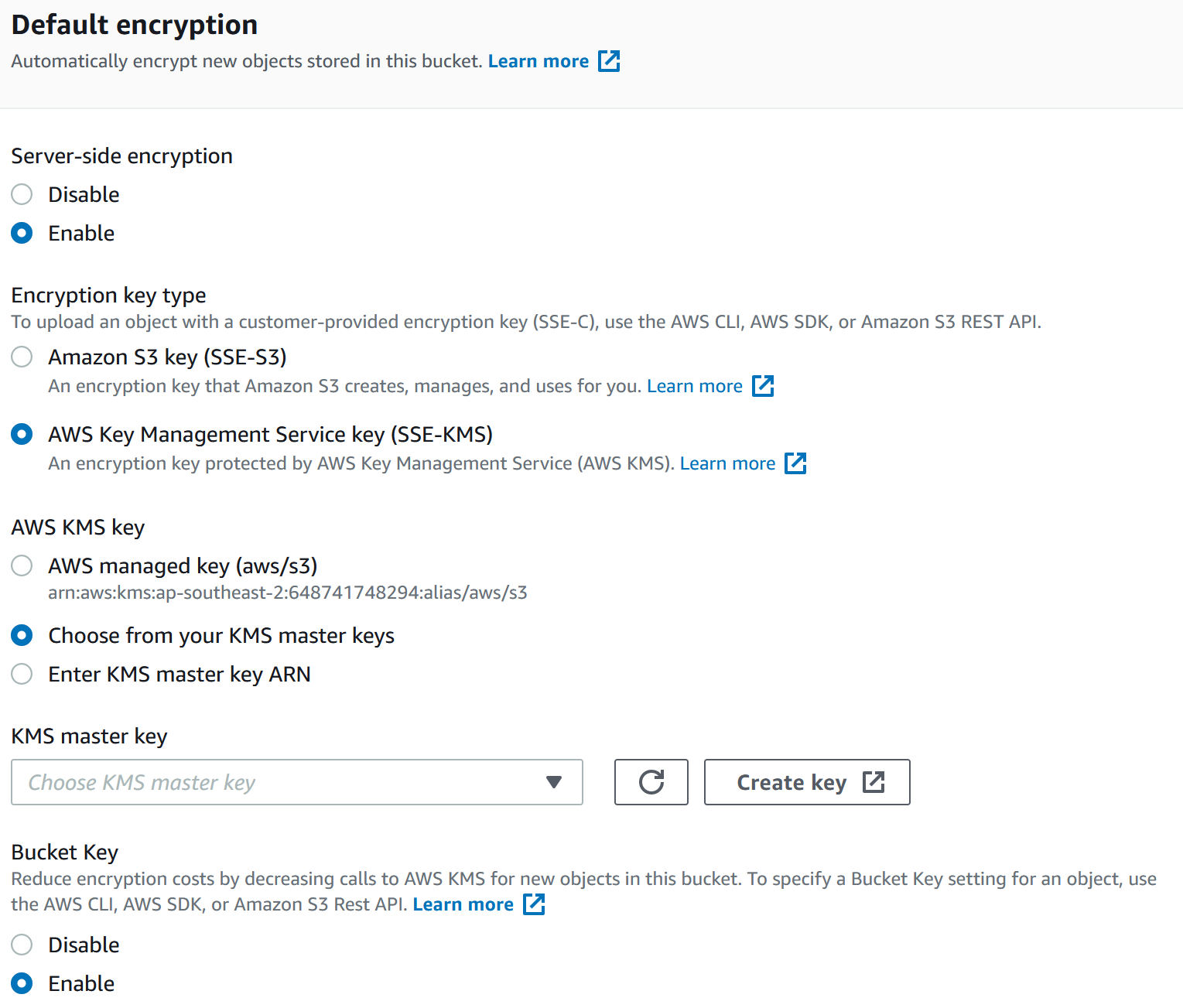
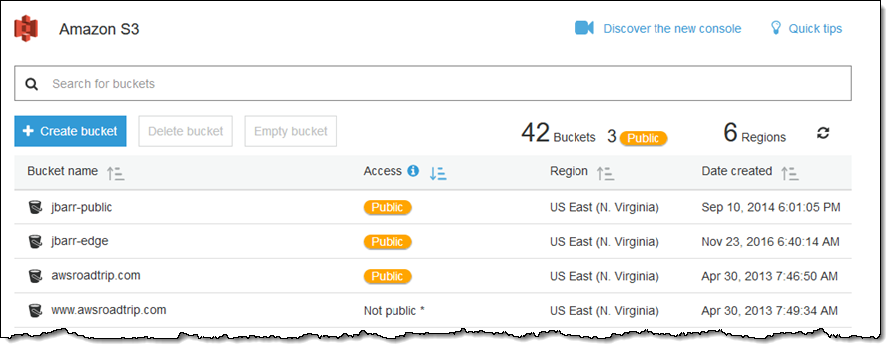
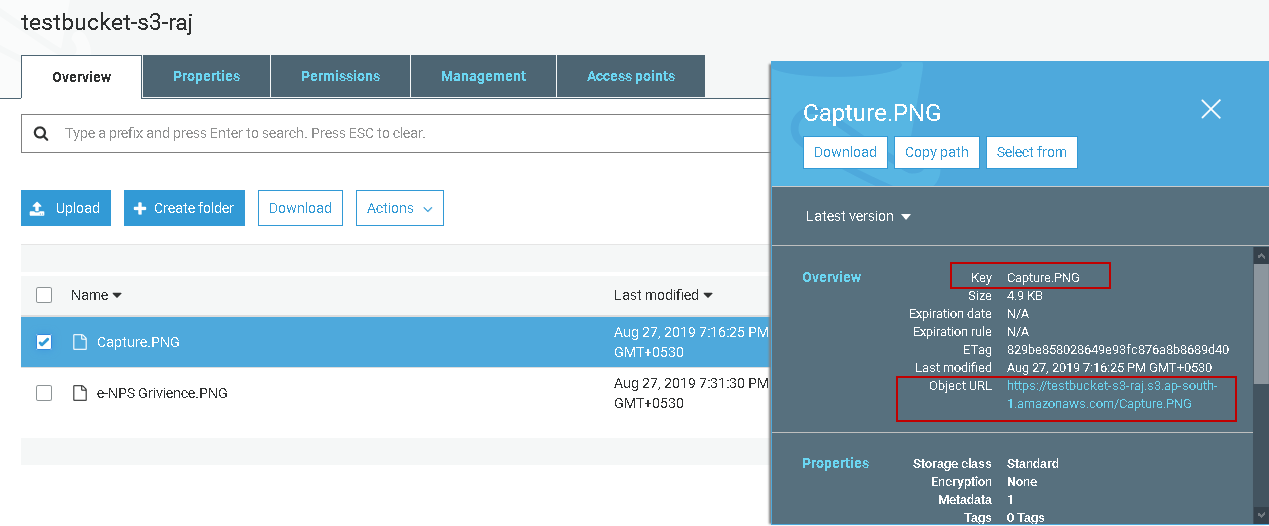
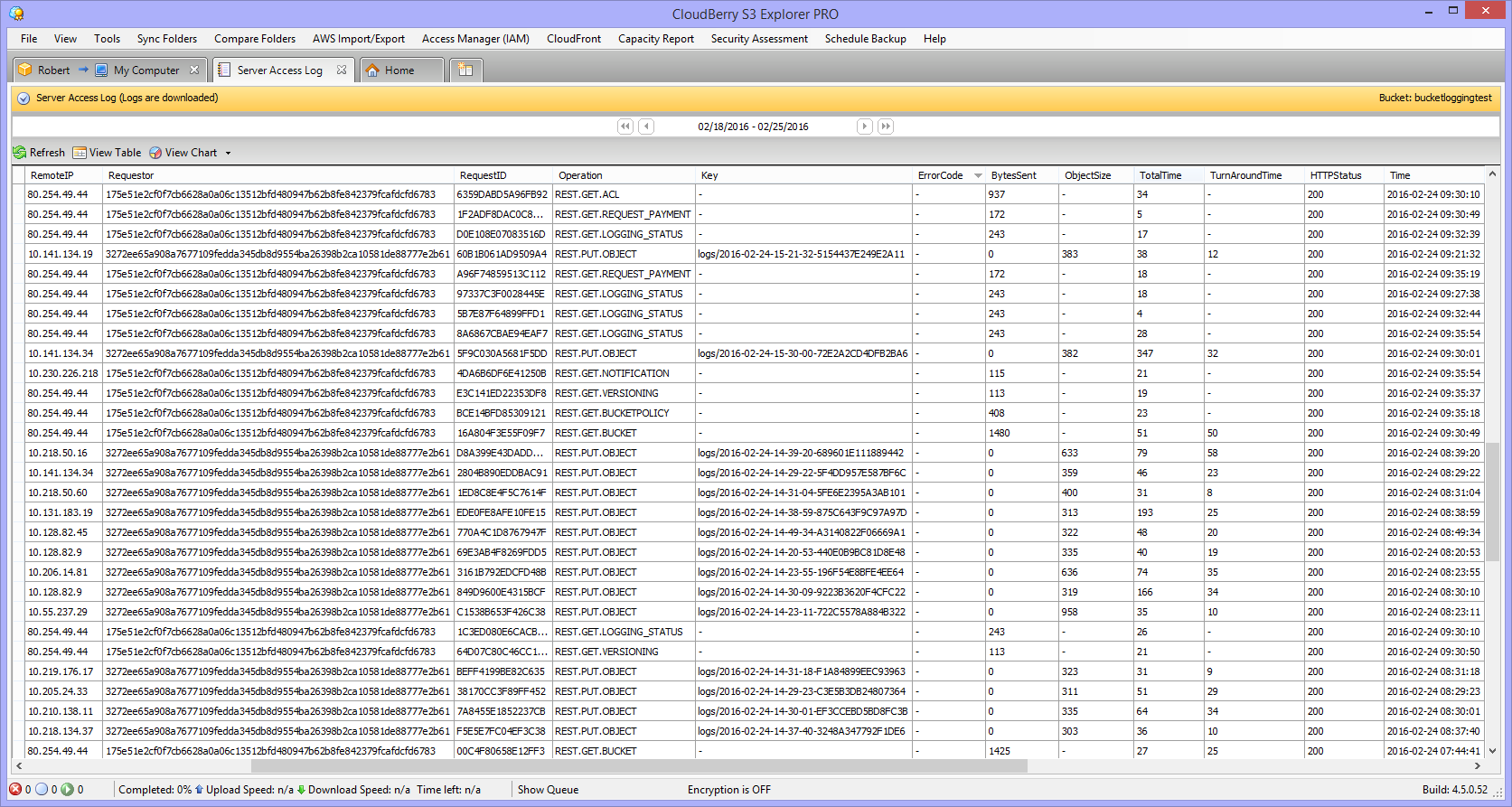
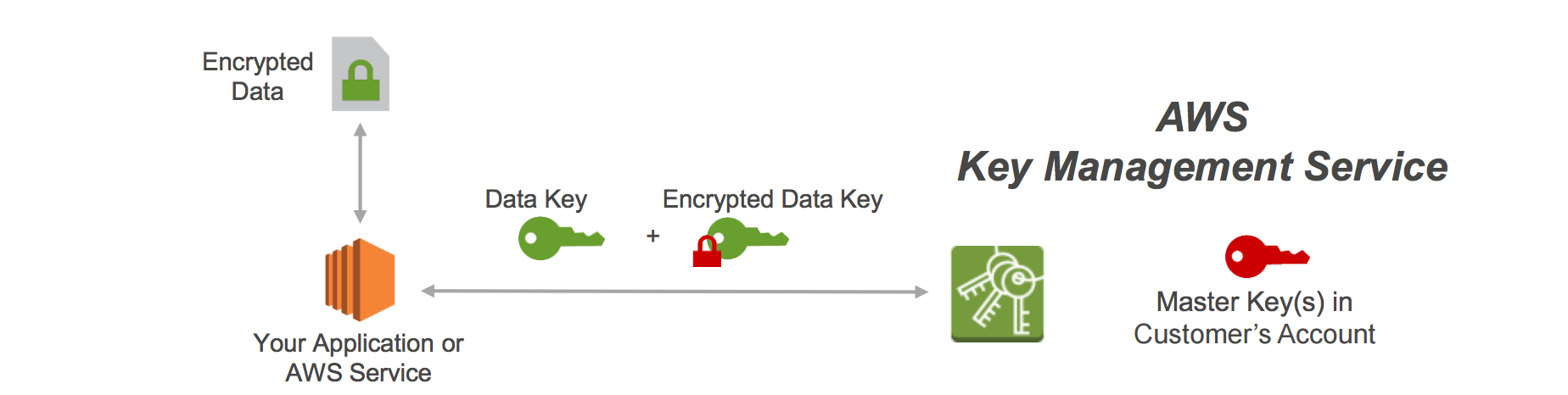
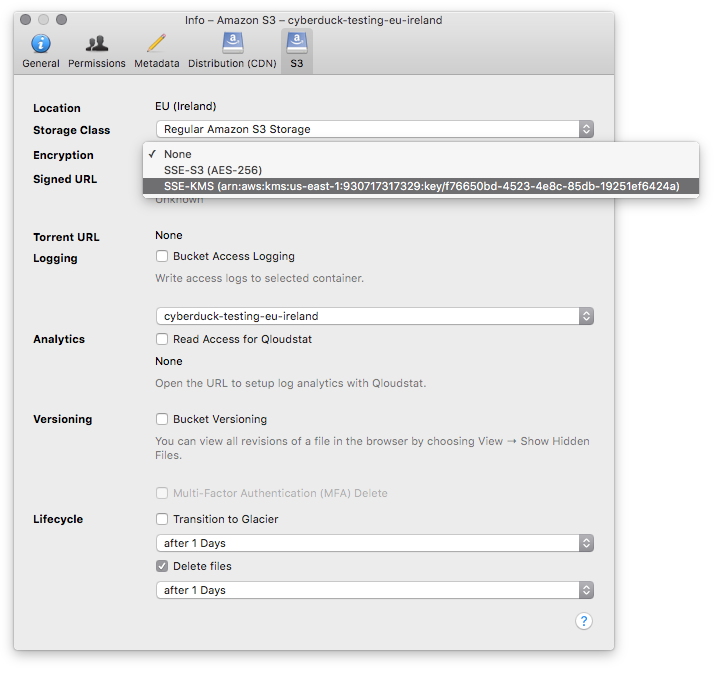
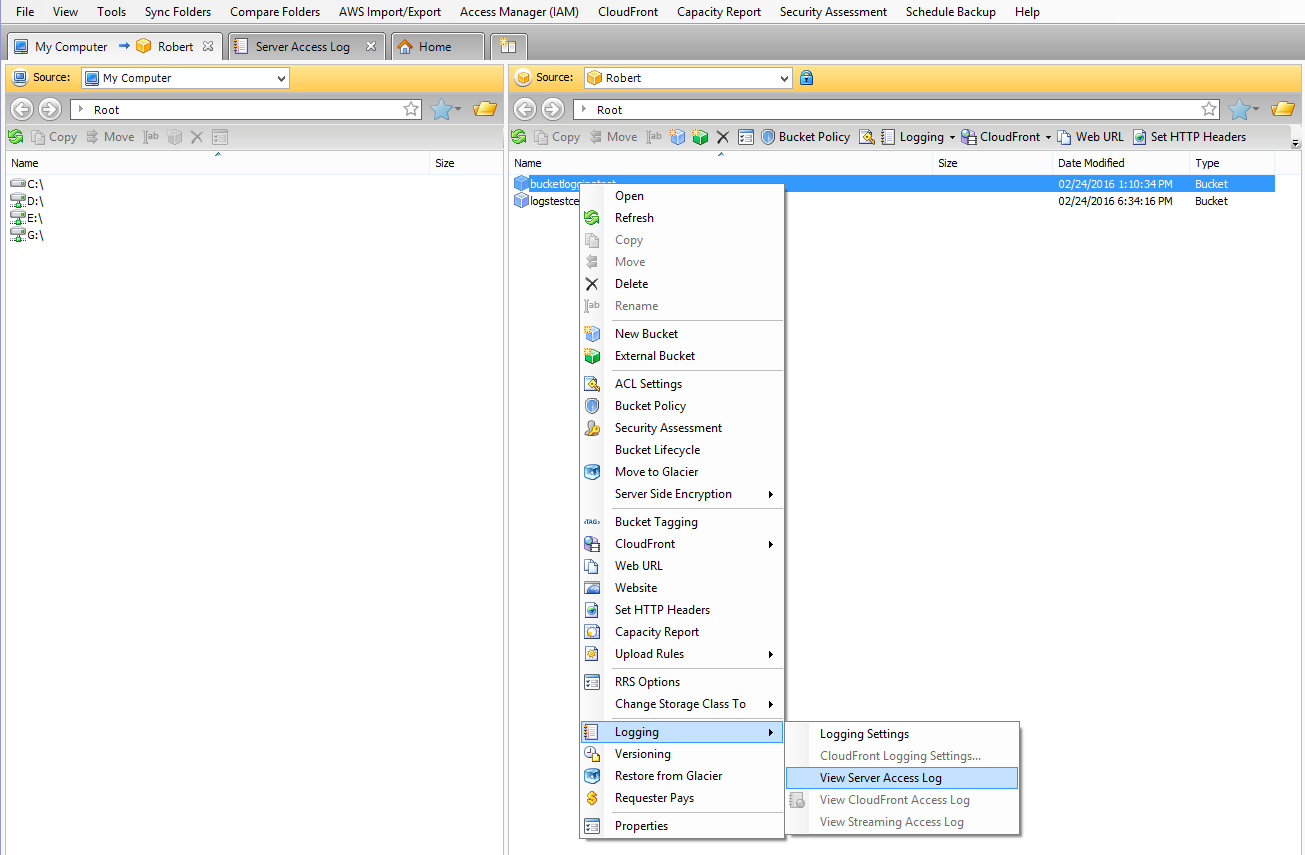
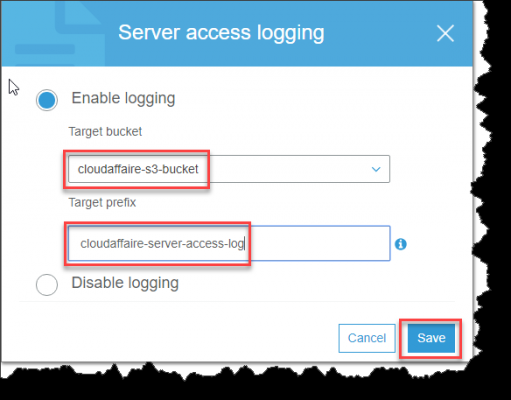
AWS S3 supports several mechanisms for serverside encryption of data S3managed AES keys (SSES3) Every object that is uploaded to the bucket is automatically encrypted with a unique AES256 encryption key Encryption keys are generated and managed by S3 Customermanaged keys stored in the AWS Key Management Service (SSEKMS) Important You can grant crossaccount access for a customer managed AWS KMS key, but not for an AWS managed AWS KMS keyThe key policy of an AWS managed AWS KMS key can't be modified 1 Open the AWS KMS console, and then view the key's policy document using the policy viewModify the key's policy to grant the IAM user permissions for theUsing the S3 console Sign in to the AWS Management Console and open the Amazon S3 console at https//consoleawsamazoncom/s3/ In the Buckets list, choose the name of the bucket that you want to enable server access logging for Choose Properties In the Server access logging section, choose Edit
Then select the S3 bucket the logs should be written into For more information, see Enabling Amazon S3 server access logging Send logs to Datadog If you haven't already, set up the Datadog log collection AWS Lambda function Once the lambda function is installed, there are two ways to collect your S3 access logsWe used S3 as a storage medium;For a small monthly object monitoring and automation charge, S3 IntelligentTiering monitors access patterns and automatically moves objects that have not been accessed to lowercost access tiers S3 IntelligentTiering automatically stores objects in three access tiers one tier that is optimized for frequent access, a 40% lowercost tier that is optimized for infrequent access,
Aws s3 access logs encryptionのギャラリー
各画像をクリックすると、ダウンロードまたは拡大表示できます
 |  |  |
 |  |  |
 |  |  |
「Aws s3 access logs encryption」の画像ギャラリー、詳細は各画像をクリックしてください。
 |  |  |
 |  |  |
 |  |  |
「Aws s3 access logs encryption」の画像ギャラリー、詳細は各画像をクリックしてください。
 |  | |
 |  |  |
 |  | |
「Aws s3 access logs encryption」の画像ギャラリー、詳細は各画像をクリックしてください。
 |  | |
 |  | |
 |  | |
「Aws s3 access logs encryption」の画像ギャラリー、詳細は各画像をクリックしてください。
 |  | |
 |  |  |
 |  |  |
「Aws s3 access logs encryption」の画像ギャラリー、詳細は各画像をクリックしてください。
 |  | |
 | ||
 |  |  |
「Aws s3 access logs encryption」の画像ギャラリー、詳細は各画像をクリックしてください。
 |  |  |
 |  |  |
 |  | |
「Aws s3 access logs encryption」の画像ギャラリー、詳細は各画像をクリックしてください。
 |  |  |
 |  | |
 |  |  |
「Aws s3 access logs encryption」の画像ギャラリー、詳細は各画像をクリックしてください。
 |  |  |
 |  | |
 |  |  |
「Aws s3 access logs encryption」の画像ギャラリー、詳細は各画像をクリックしてください。
 |  | |
 |  |  |
 |  |  |
「Aws s3 access logs encryption」の画像ギャラリー、詳細は各画像をクリックしてください。
 | ||
 |  |  |
 |  |  |
「Aws s3 access logs encryption」の画像ギャラリー、詳細は各画像をクリックしてください。
 |  |  |
 |  |
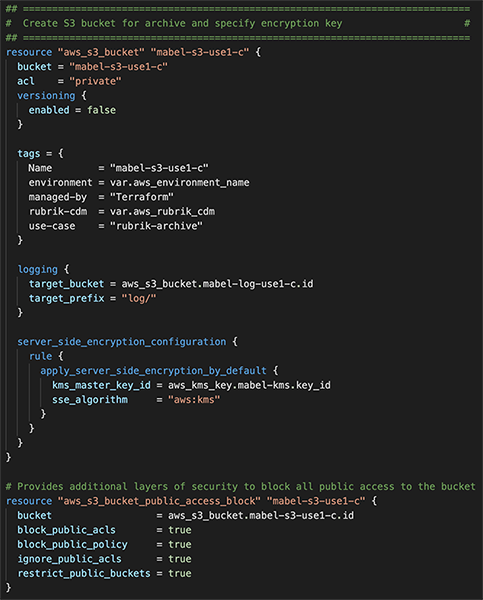
It implements a configurable log retention policy, which allows you to efficiently manage logs across different storage classes ( eg Glacier) and ultimately expire the data altogether It enables serverside default encryption https//docsawsamazoncom/AmazonS3/latest/dev/bucketencryptionhtml To storage your AWS ELB access log to ASW S3 We use Terraform template below the below Create a new S3 bucket called "elblogdavidwzhangcom" Define a bucket policy which grant Elastic Load Balancing access to the newly created S3 bucket "elblogdavidwzhangcom" As you know, each AWS region has its own account ID for Elastic Load Balancing
Incoming Term: aws s3 access logs encryption,
コメント
コメントを投稿